Let’s take a look at what a Code Signing certificate is and its role in code security
Before we get down to what a Code Signing certificate is and what it does, let’s go through a few familiar images first.
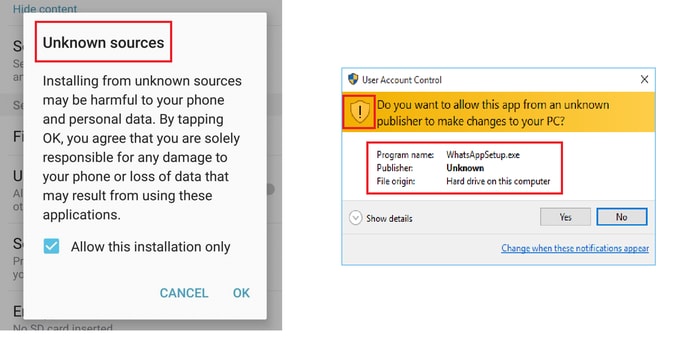
Unless you’re an alien, you’d definitely relate to these images. Chances are, you’d have clicked Yes/OK without giving it a thought. But what is the reason behind such warnings? What do they really mean?
Let’s understand.
Code Signing certificate and why we need it
A Code Signing certificate is a digital certificate that vouches for the legitimacy of code, software, app, and executables. Based on Public Key Infrastructure, a Code Signing certificate signs the code and makes sure that it doesn’t get altered or corrupted on the way from the developer’s system to the end user’s system. This way, Code Signing helps the end-users ascertain whether software/app can be trusted or not.
Therefore, we can say that Code Signing fulfills two fundamental objectives – Validation and Integrity. Validation because it shows that software has been written by a legitimate and verified publisher. Code signing certificate doesn’t let any 3rd party alter and corrupt the code behind any software. Thereby, serving the purpose of code integrity.
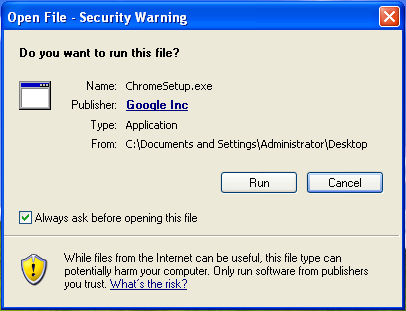
For example, if you download Chrome from its official website, you’ll see Google Inc. as the publisher.
How does Code Signing work?
A Code Signing certificate works on an encryption technique called Public Key Infrastructure (PKI) which is similar to the method used in SSL/TLS certificates. Two cryptographic keys, namely a public key and a private key are used to encrypt the code. This public-private key pair is generated when the software author requests a certificate from a certificate authority (CA). Out of the two keys, the private key signs the data/code and the public key is used to authorize the signature.
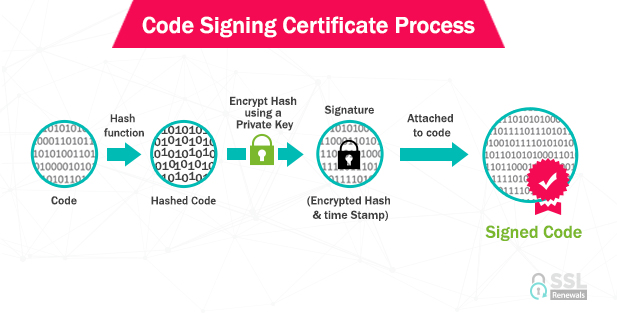
The Private Key is kept by the publisher so that the software remains intact and no hacker could tamper with it. Once the certificate provider gets the request from the applicant, it verifies the identity of the applicant. Once the vetting process is done by the CA, the certificate is deemed legitimate and the certificate is issued.
Validate your code with a Code Signing Certificate at a whopping discount
The path towards warning-free application downloads is here. Activate your discount today and save up to 50%.
Software/App Code security wth Code Signing Certificate starts at $83
The Code Signing Process
If you want to sign software using a code signing certificate, you must follow these steps:
- First, you must apply for a code signing certificate from a trusted certificate authority (CA).
- Then you should get your identity verified by the CA.
- The next step in line is to generate a one-way hash and use your private key to encrypt it.
- Last, you have to bundle the hash and certificate.
How Code Signing prevents malware proliferation
Open-source software has proved to be a lethal weapon from a hackers’ point of view. Infusing malware in such software has been a tried and tested method. Therefore, we strongly recommend you avoid software that displays unknown publishers and stay away from the danger.
However, it doesn’t mean that digitally signed software is one hundred percent bulletproof. We’ve seen cases of malware implanted in signed software, too. CCleaner, an extensively used software fell victim to it just recently.
Such an infusion of malware is mostly done by stealing the certificates/private keys. Therefore, you must keep your code signing certificate at secure places and make sure all files are password protected.
Types of Code Signing certificates and their validation requirements
Primarily, there are two types of code signing certificates – organization validation (OV) and individual validation (IV). As their names clearly advocate, OV certs are used to validate organizations and IV certs are used for the individual developers.
Organization Validation code signing requirements
If you want to issue an OV certificate, there are four general requirements that you must prove to the CA.
- Organization Authentication
- Locality Presence
- Telephone Verification
- Final Verification Call
Individual Validation code signing requirements
If you’re a lone wolf, these are the requirements that you must take care of.
- Identity Verification
- Telephone Verification
- Final Verification Call
| Product Name | Discount | Price | Details |
|---|---|---|---|
| Comodo Code Signing | Get Additional 48% OFF | $87.00/Yr | Add To Cart |
| Thawte Code Signing | Get Additional 84% OFF | $124.17/Yr | Add To Cart |
| Symantec Code Signing | Get Additional 48% OFF | $365.83/Yr | Add To Cart |
| Sectigo Code Signing | Get Additional 50% OFF | $82.67/Yr | Add To Cart |
Final thoughts
Code Signing is an essential method that protects users as well as developers. From a developer’s point of view, code signing not only protects the code, but it also enhances your reputation as well. This ultimately leads to better download numbers. If you’re a user, you must insist on downloading software that is signed.








 (5 votes, average: 4.20 out of 5, rated)
(5 votes, average: 4.20 out of 5, rated)